What is Risk Management in Supplier Shield?
Let's break down the key concepts:
- Risk Exposure (BIA)
- Rating
- Risk Level
- Functions
Use these individually or together to get a clear picture of your supply chain risks.
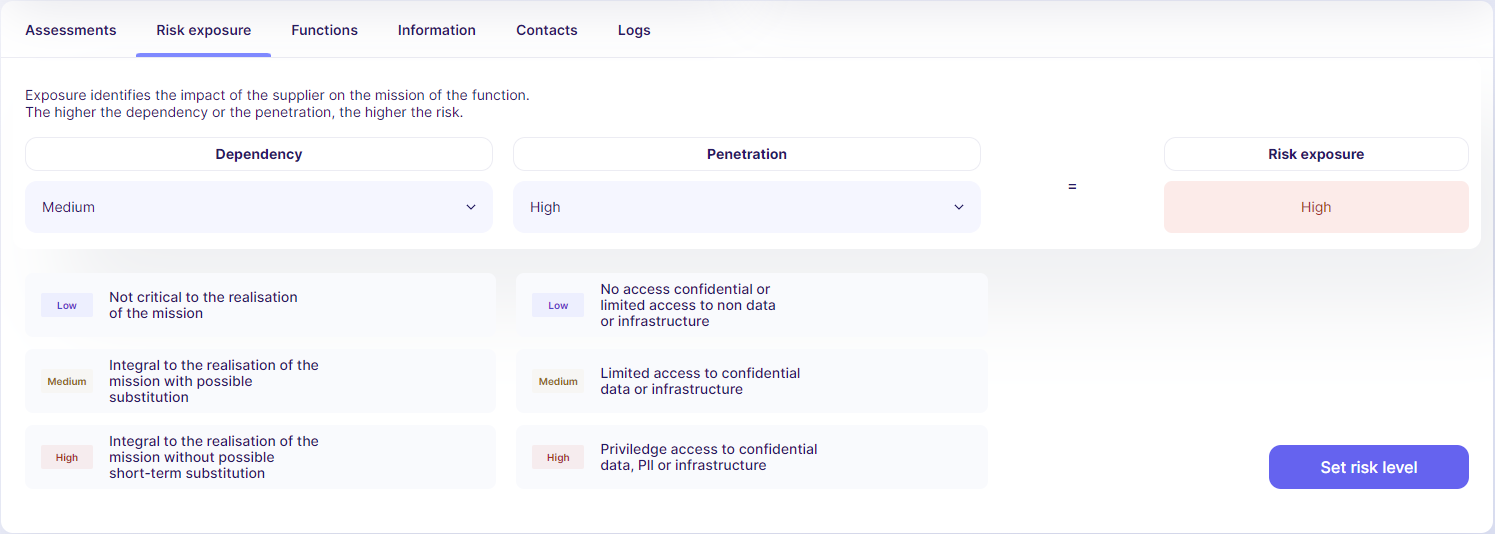
Risk Exposure
Risk exposure considers two main factors:
- Dependence: How crucial a supplier is for your operations.
- Penetration: How much access a supplier has to your data or systems (like PII or IP).
Based on EBIOS principles, this method allows for effective Business Impact Assessment (BIA). The risk exposure is calculated automatically from the level of dependence and penetration you choose. Find this feature on each supplier’s page.
Note: This feature is only available with Business and Enterprise subscriptions.
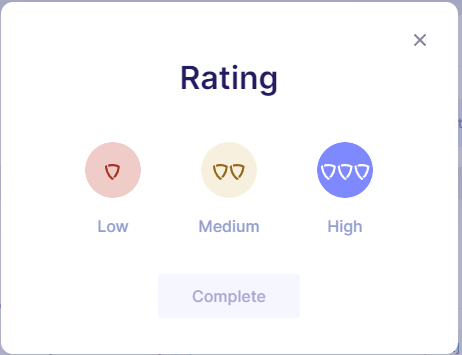
Rating
A rating is given at the end of an assessment, either by you (for a self-assessment) or by your Supplier Shield expert team if you've chosen the PRO version. When the assessment is complete, a pop-up lets you select a rating, with more shields indicating better security. The latest rating will be displayed next to the supplier's name, along with the risk exposure.
Risk Level
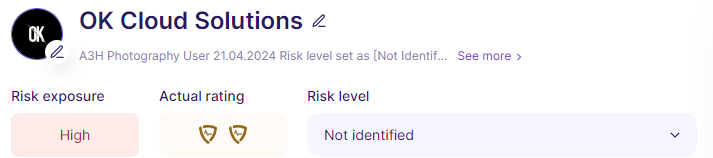
The risk level is your overall perception of a supplier's risk, combining the risk exposure and the rating. You can adjust this level at anytime.
Functions
Functions link your suppliers to your business processes or operations. Read more about this in the How to organise your suppliers article. The colour of each function changes based on the risk level you set, allowing you to identify potential risks quickly if a supplier is non-compliant or underperforming.
